Welcome!
Fun with Forensics, Pentesting & Gummy Bears
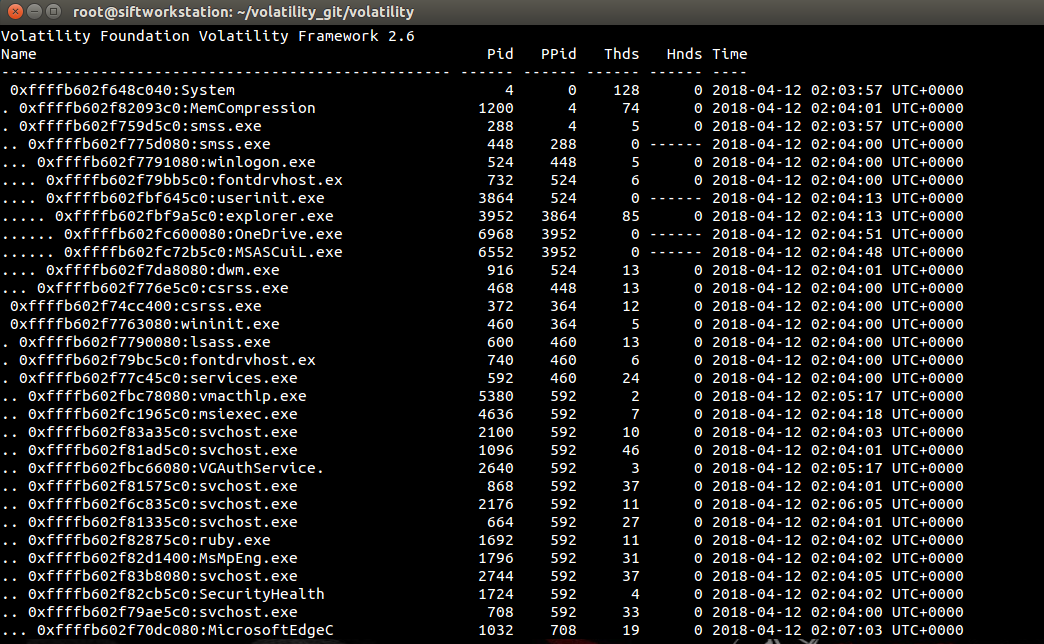
Topics one might find here:
Offensive Forensics
How attackers utilize digital forensics in order to gather information, elevate their privileges and more, in order to pursue their goals.
How attackers utilize digital forensics in order to gather information, elevate their privileges and more, in order to pursue their goals.
Computer Networks
General topics concerning computer networks and interconnected systems. Maybe start with some artisanal raw TCP/IP packets.
General topics concerning computer networks and interconnected systems. Maybe start with some artisanal raw TCP/IP packets.
General IT Security Stuff
Random IT security topics that don’t fit anywhere else.
Random IT security topics that don’t fit anywhere else.
Sharing knowledge is one of the key principles of our information security community. However, learning IT security, and especially forensics, often feels like drinking from a water hose. By focusing on the fundamentals and breaking down complexity to the basics, this website aims to be a source of knowledge for everyone interested learning new topics or recap already known material.