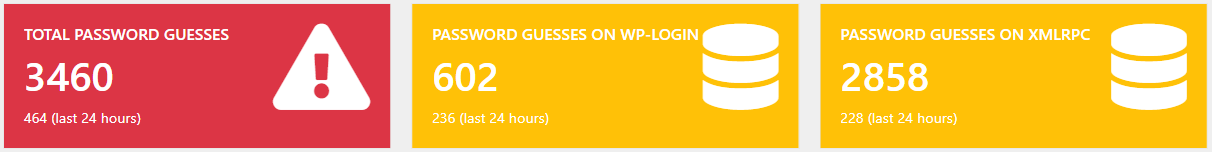
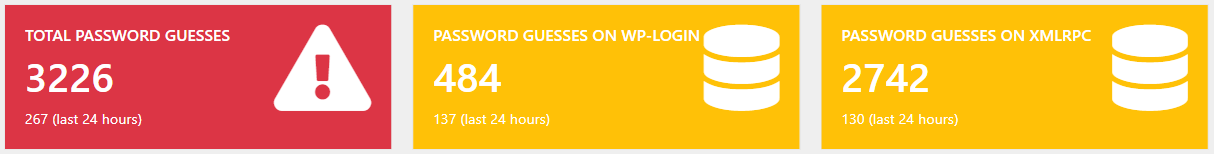
When playing around with a small web honeypot I’m developing, I noticed an interesting brute-force attack on a test deployment. There were 267 password guessing attacks on the WordPress section of the honeypot in the last 24 hours. They were equally distributed between the wp-login.php (default login via browser) being attacked 137 times and the xmlrpc.php (WordPress XML API) attacked 130 times.
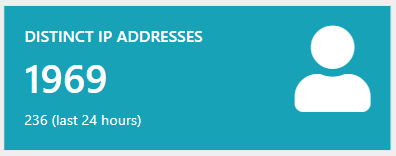
This alone is already an interesting observation on its own, since usually this is heavily skewed in either one or the other direction. The most surprising number however is the distinct IP addresses accessing the honeypot in the last 24 hours:
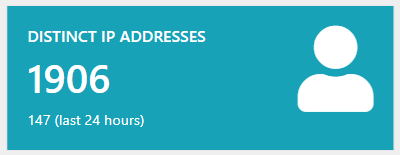
147 different IP addresses in the last 24 hours. This number looks suspiciously similar to the number of password guesses on the two endpoints. When looking closer and the requests made, a pattern occurred:
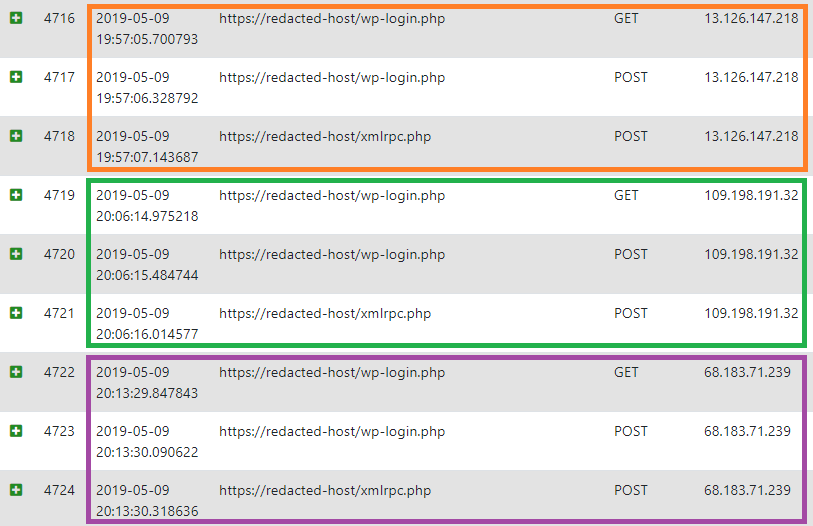
Every IP address performed only three requests:
- GET request to
wp-login.php - POST request to
wp-login.php-> password guessing attack - POST request to
xml-rpc.php-> password guessing attack
There was always a GET requests to the wp-login.php page of WordPress first, followed by a POST login request with a password guess, then followed by a POST request to the xmlrpc.php also performing a password guess. Beside those three, no other requests were made from those IPs.
Quick Analysis – GeoIp + Whois
A very brief GeoIP and Whois lookup with Just-Metadata resulted in the following information:
Top 10 Countries =================================== United States : 42 France : 13 Singapore : 12 India : 10 Vietnam : 8 Germany : 8 Netherlands : 6 United Kingdom : 5 China : 5 Japan : 4 Top 10 ISPs =================================== DigitalOcean, LLC : 47 Amazon.com, Inc. : 7 OVH ISP : 6 Online S.A.S. : 5 Amazon Technologies Inc. : 5 OVH SAS : 4 Shenzhen Tencent Computer Systems Company Limited : 3 Google LLC : 3 GoDaddy.com, LLC : 3 1&1 Internet SE : 2
I have uploaded a list of 145 IP addresses performing those requests.
Edit:
As of writing this post (UTC: 2019-05-10 14:16), the probing is still ongoing:
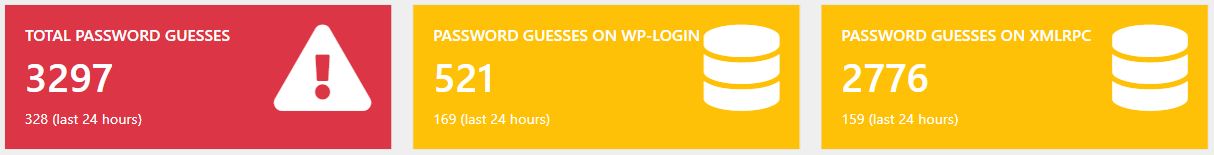
Edit 2:
UTC 2019-05-10 16:30